New MS-100 dumps are truly valid exam material for passing the Microsoft 365 Identity and Services exam. And you can always buy the latest MS-100 dumps – helping you pass your Microsoft 365 Identity and Services exam in time.
The leads4pass MS-100 dumps contain 378 real and valid exam questions and answers that you can easily study in any environment. MS-100 dumps with PDF and VCE are included to make it easier for candidates to learn and practice.
New MS-100 Dumps exam material has been updated and reviewed by the most dedicated certification experts to ensure you successfully pass the Microsoft 365 Identity and Services exam.
New MS-100 Dumps exam success rate is industry-recognized and field-proven. If you are preparing to take the Microsoft 365 Identity and Services exam, your first choice should be leads4pass MS-100 Dumps https://www.leads4pass.com/ms-100.html.
Microsoft MS-100 free dumps to help you try it first
QUESTION 1
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn\’t matters how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information Use the following login credentials as needed:
To enter your username, place your cursor in the Sign inbox and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:[email protected]
Microsoft 365 Password: 3andYWyjse-6-d
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 10887751
You plan to allow the users in your organization to invite external users as guest users to your Microsoft 365 tenant.
You need to prevent the organization\’s users from inviting guests who have an email address that uses a [email protected].
A. See below.
Correct Answer: A
You need to add gmail.com as a denied domain in the ‘External collaboration settings’.
1.
Go to the Azure Active Directory admin center.
2.
Select Users then select ‘User settings’.
3.
Under External Users, select the ‘Manage external collaboration settings.
4.
Under ‘Collaboration restrictions’, select the ‘Deny invitations to the specified domains’ option.
5.
Under, Target Domains, type in the domain name ‘gmail.com’
6.
Click the Save button at the top of the screen to save your changes.
References: https://docs.microsoft.com/en-us/azure/active-directory/b2b/allow-deny-list
QUESTION 2
HOTSPOT
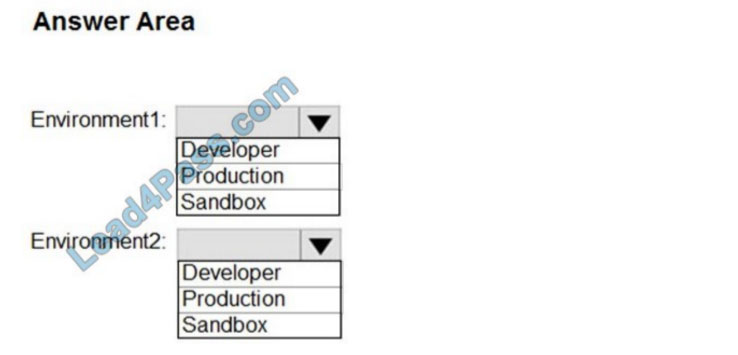
You plan to deploy two Microsoft Power Platform environments as shown in the following table.

Which environment type should you use for each environment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
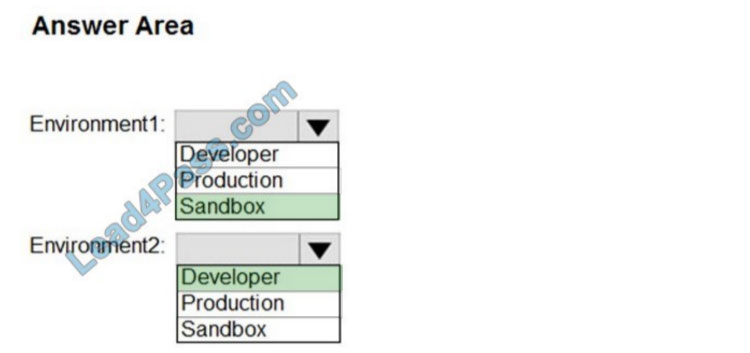
Reference: https://docs.microsoft.com/en-us/power-platform/admin/environments-overview
QUESTION 3
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn\’t matters how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information Use the following login credentials as needed:
To enter your username, place your cursor in the Sign inbox and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username: [email protected]
Microsoft 365 Password: oL9z0=?Nq@ox
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 11098651
You need to ensure that all the users in your organization are prompted to change their passwords every 180 days.
To answer the question, sign in to the Microsoft 365 portal.
Correct Answer: See below.
You need to configure the Password Expiration Policy.
1. Sign in to the Microsoft 365 Admin Center.
2. In the left navigation pane, expand the Settings section then select the Settings option.
3. Click on Security and Privacy.
4. Select the Password Expiration Policy.
5. Ensure that the checkbox labeled “Set user passwords to expire after a number of days” is ticked.
6. Enter 180 in the “Days before passwords expire” field.
7. Click the ‘Save changes’ button.
QUESTION 4
HOTSPOT
You have a Microsoft 365 subscription that uses a default domain named litwareinc.com. The subscription has a Microsoft SharePoint site collection named Collection1.
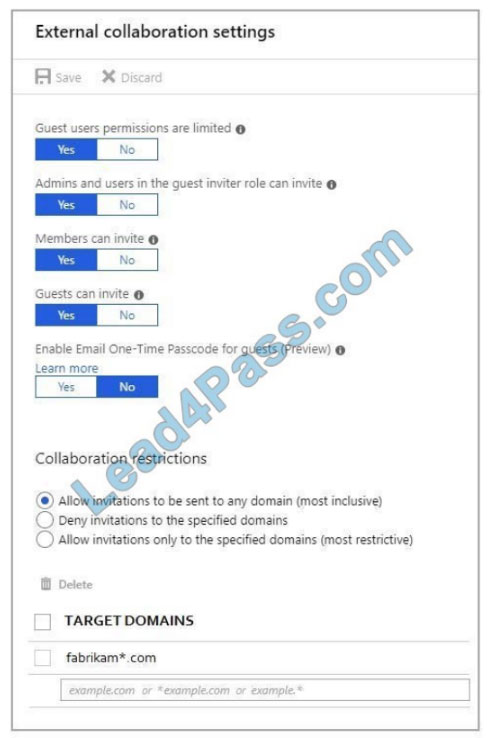
From the Azure Active Directory admin center, you configure the External collaboration settings as shown in the External Collaboration Settings exhibit. (Click the External Collaboration Settings tab.)
From the SharePoint admin center, you configure the sharing settings as shown in the SharePoint Sharing exhibit. (Click the SharePoint Sharing tab.)
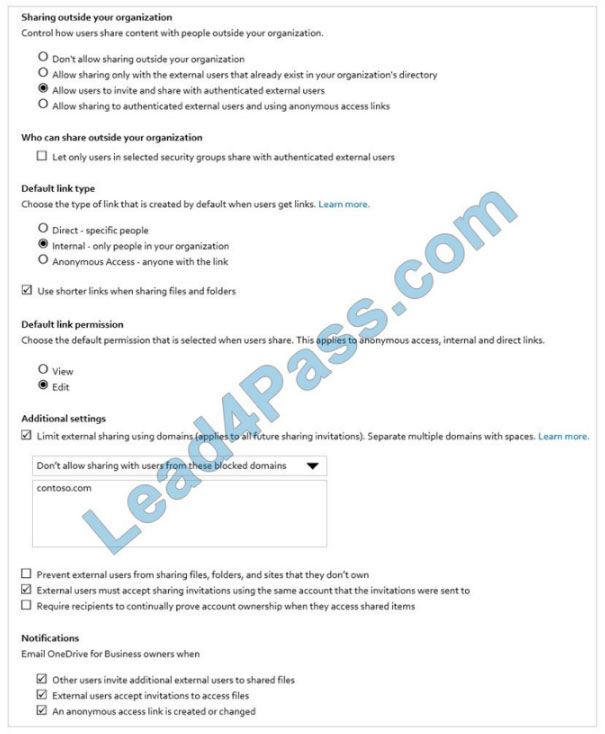
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
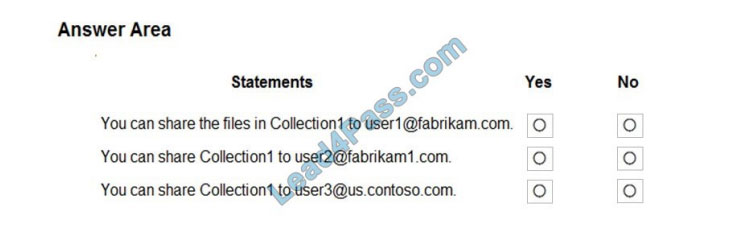
Correct Answer:
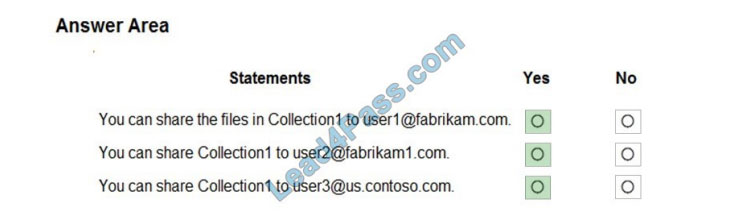
Box 1: Yes
In the first exhibit, “Allow invitations to be sent to any domain (most inclusive) is enabled”. Also, everyone is allowed to ‘invite’. The Target Domains setting will have no effect. This would only apply if one of the Allow/Deny invitations to the specified domain options were selected.
There is a restriction that blocks invitations from being sent to contoso.com. However, this restriction does not apply to Fabrikam.com. Therefore, you can share the files in Colection1 to [email protected].
Box 2: Yes
As noted above, external sharing is enabled for any domain except contoso.com. The Target Domains setting in the first exhibit will have no effect. Therefore, you can share Collection1 with [email protected].
Box 3: Yes
As noted above, external sharing is enabled for any domain except contoso.com. Blocking sharing to contoso.com does not block sharing to us.contoso.com. Therefore, you can share Collection1 with [email protected].
Reference: https://docs.microsoft.com/en-us/sharepoint/turn-external-sharing-on-or-off
QUESTION 5
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear on the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following
requirements:
1. Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
2. User passwords must be 10 characters or more.
Solution: Implement pass-through authentication and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
This solution does not meet the following requirement:
Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
This is because, with pass-through authentication, the authentication is performed by the on-premise Active Directory.
This solution does meet the following requirement:
User passwords must be 10 characters or more.
Configuring the Default Domain Policy in the on-premise Active Directory meets the requirement.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-password-hash-synchronization
QUESTION 6
You need to consider the underlined segment to establish whether it is accurate.
You have recently configured a conditional access policy to force mobile device users to use multi-factor authentication when accessing Microsoft SharePoint.
To check who used multi-factor authentication to authenticate, you view the Usage reports from the Azure Active Directory admin center.
Select adjustment required if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
A. No adjustment is required
B. user sign-ins
C. event logs
D. audit logs
Correct Answer: B
References: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-reporting
QUESTION 7
Your company has an Active Directory domain as well as a Microsoft Azure Active Directory (Azure AD) tenant.
After configuring directory synchronization for all users in the organization, you configure a number of new user accounts to be created automatically.
You want to run a command to make sure that the new user accounts synchronize to Azure AD in the shortest time required.
Which of the following is the command that you should use?
A. New-ADSyncRule
B. Set-ADSyncSchedulerConnectorOverride
C. Start-ADSyncSyncCycle
D. Set-ADSyncSchema
Correct Answer: C
QUESTION 8
Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.

A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 all open files that have the .abc file extension. You implement Windows Information Protection (WIP) by using the following configurations:
1.
Exempt apps: App2
2.
Protected apps: App1
3.
Windows Information Protection mode: Block
4.
Network boundary: IPv4 range of 192.168.1.1-192.168.1.255
You need to identify the apps from which you can open File1.abc
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
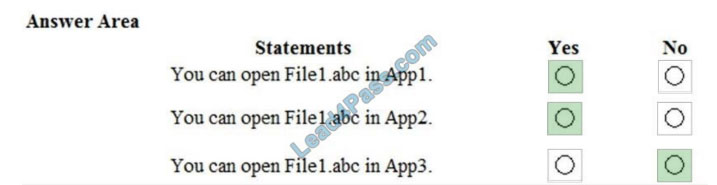
Box 1: Yes.
App1 is a protection app in the Windows Information Protection policy. File1 is stored on Server1 which is in the Network Boundary defined in the policy. Therefore, you can open File1 in App1.
Box 2: Yes.
App2 is exempt from the Windows Information Protection policy. The protection mode in the policy is blocking so all apps that are not included in the policy cannot be used to open the file… except for exempt apps. Therefore, you can open File1 in App2.
Box 3: No.
The protection mode in the policy is blocking so all apps that are not included in the policy as protected apps or listed as exempt from the policy cannot be used to open the file. Therefore, you cannot open File in App3.
References:
QUESTION 9
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
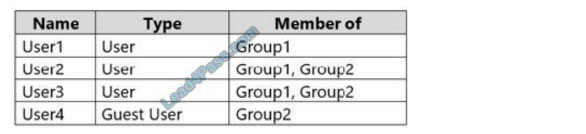
User1 is the owner of Group1. User2 is the owner of Group2.
You create an access review that contains the following configurations:
1. Users to review: Members of a group
2. Scope: Everyone
3. Group: Group1, Group2
4. Reviewers: Group owners
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
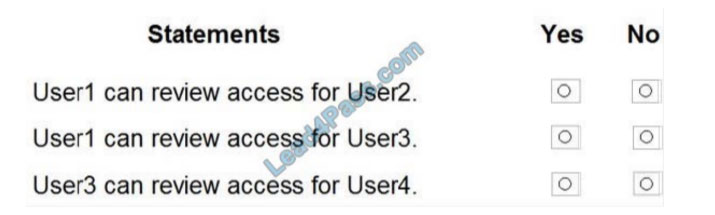
Correct Answer:
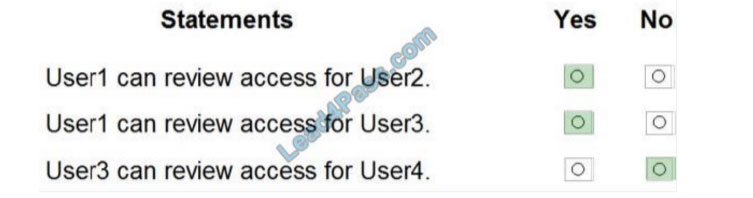
Box 1: Yes
User1 is the owner of Group1. User2 is in Group1 and Group2. Group owners can review access. Therefore, User1 can review User2\’s membership in Group1.
Box 2: Yes
User1 is the owner of Group1. User3 is in Group1 and Group2. Group owners can review access. Therefore, User1 can review User3\’s membership in Group1.
Box 3: No
Only group owners can review access. User3 is not a group owner. Therefore, User3 cannot review the membership of the groups.
References:
https://docs.microsoft.com/en-us/azure/active-directory/governance/create-access-review
QUESTION 10
You need to ensure that all the sales department users can authenticate successfully during Project1 and Project2.
Which authentication strategy should you implement for the pilot projects?
A. password hash synchronization and seamless SSO
B. pass-through authentication
C. password hash synchronization
D. pass-through authentication and seamless SSO
Correct Answer: A
1.
Project1: During Project1, the mailboxes of 100 users in the sales department will be moved to Microsoft 365.
2.
Project2: After the successful completion of Project1, Microsoft Teams and Skype for Business will be enabled in Microsoft 365 for the sales department users.
3.
After the planned migration to Microsoft 365, all users must be signed in to on-premises and cloud-based applications automatically.
4.
Fabrikam does NOT plan to implement an identity federation.
5.
After the planned migration to Microsoft 365, all users must continue to authenticate to their mailbox and to SharePoint sites by using their UPN.
You need to enable password hash synchronization to enable the users to continue to authenticate to their mailbox and to SharePoint sites by using their UPN.
You need to enable SSO to enable all users to be signed in to on-premises and cloud-based applications automatically.
References: https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
QUESTION 11
You create a Microsoft 365 subscription.
You plan to deploy Microsoft Office 365 ProPlus applications to all the client computers at your company.
You prepare the following XML file for the planned deployment.
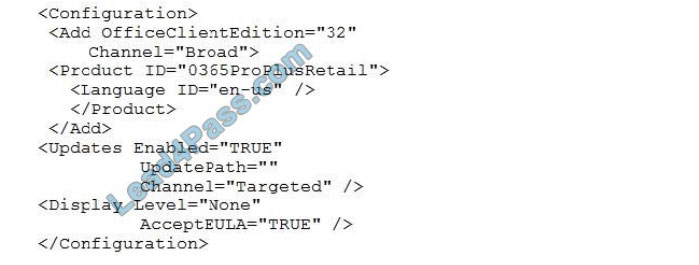
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
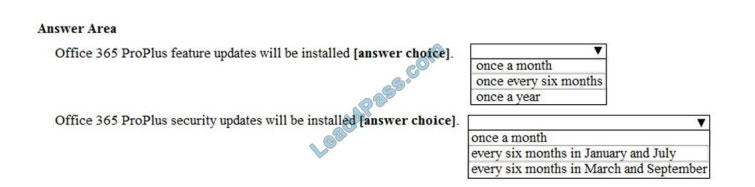
Correct Answer:
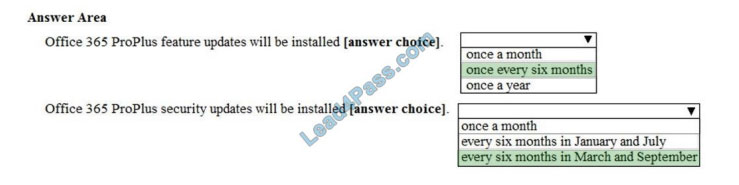
Box 1:
Office 365 ProPlus feature updates will be installed once every six months.
The Channel element in the configuration file is set to ‘Targeted’. This means Semi-Annual Targeted.
To help your organization prepare for a Semi-Annual Channel release, Microsoft provides a Semi-Annual Channel (Targeted). The primary purpose of this update channel is to give pilot users and application compatibility testers in your organization a chance to work with the upcoming Semi-Annual Channel release
Box 2:
Office 365 ProPlus security updates will be installed every six months in March and September.
A Semi-Annual Channel (Targeted) release with new features is expected to be released twice a year, in March and September.
The March and September feature releases for the Semi-Annual Channel (Targeted) also include security and non-security updates that have been released previously in the Monthly Channel.
Reference: https://docs.microsoft.com/en-us/deployoffice/configuration-options-for-the-office-2016-deployment-tool#updates-element
https://docs.microsoft.com/en-us/deployoffice/overview-of-update-channels-for-office-365-proplus
QUESTION 12
SIMULATION
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn\’t matters how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information Use the following login credentials as needed:
To enter your username, place your cursor in the Sign inbox and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:[email protected]
Microsoft 365 Password: 3andYWyjse-6-d
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 10887751
You need to create a group named Group2. Users who are added to Group2 must be licensed automatically for Microsoft Offline 365.
A. See below.
Correct Answer: A
You need to create the group and assign a license to the group. Anyone who is added to the group will automatically be assigned the license that is assigned to the group.
1.
Go to the Azure Active Directory admin center.
2.
Select the Azure Active Directory link then select Groups.
3.
Click the New Group link.
4.
Select ‘Security’ as the group type and enter ‘Group2’ for the group name.
5.
Click the Create button to create the group.
6.
Back in the Groups list, select Group2 to open the properties page for the group.
7.
Select ‘Licenses’.
8.
Select the ‘+ Assignments’ link.
9.
Tick the box to select the license.
10.
Click the Save button to save the changes.
References: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/licensing-groups-assign
QUESTION 13
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications App1, App2, and App3. The Apps use files that have the same file extensions.
Your company uses Windows Information Protection (WIP). WIP has the following configurations:
1.
Windows Information Protection mode: Silent
2.
Protected apps: App1
3.
Exempt apps: App2
From App1, you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.
Hot Area:
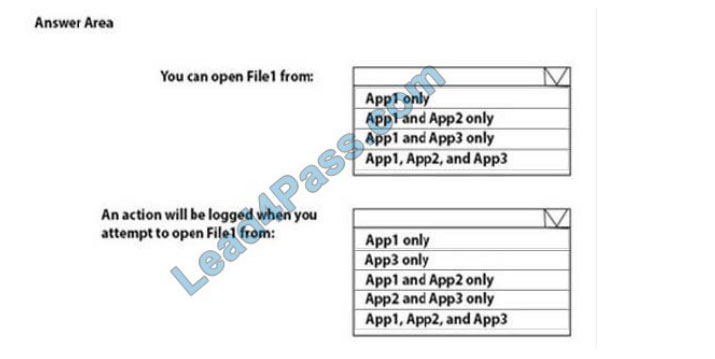
Correct Answer:
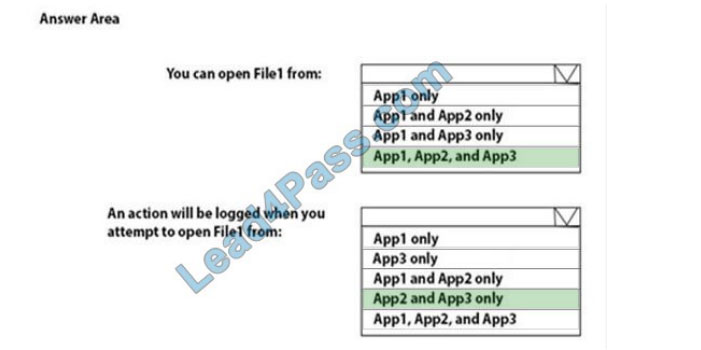
Exempt apps: These apps are exempt from this policy and can access corporate data without restrictions.
Windows Information Protection mode: Silent: WIP runs silently, logging inappropriate data sharing, without stopping anything that would’ve been prompted for employee interaction while in Allow overrides mode. Unallowed actions, like apps inappropriately trying to access a network resource or WIP-protected data, are still stopped.
Reference:
https://docs.microsoft.com/en-us/intune/apps/windows-information-protection-policy-create https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/create-wip-policy-using-intune-azure
……
Microsoft MS-100 Free Dumps online download: https://drive.google.com/file/d/1DgsinmNuuXi4LNe9ikoOH9-d2vCFcvvV/view?usp=sharing
The new MS-100 Dumps is truly valid exam material for passing the Microsoft Dynamics 365 Marketing exam. The 378 MS-100 Dumps exam questions are truly valid material for you to solve in the exam room.
Even if you are a novice, you can choose MS-100 dumps with 100% confidence:https://www.leads4pass.com/ms-100.html. Guaranteed to pass the Microsoft 365 Identity and Services exam with ease.

